That looks to me more like it's Amazon removing them, assuming that's happening when you load the page. They probably remove them so that people don't copy and share affiliated links so that they don't have to pay out more to their affiliates program.
- Posts
- 17
- Comments
- 69
- Joined
- 3 yr. ago
- Posts
- 17
- Comments
- 69
- Joined
- 3 yr. ago
- JumpDeleted
Permanently Deleted
Technology @lemmy.world Mozilla’s new CEO is doubling down on an AI future for Firefox
Firefox @lemmy.ml Mozilla’s new CEO is doubling down on an AI future for Firefox
Rust Programming @lemmy.ml The end of the kernel Rust experiment
Rust @programming.dev The end of the kernel Rust experiment
Firefox @lemmy.ml Firefox 147 Will Support The XDG Base Directory Specification
Steam Hardware @sopuli.xyz Steam Controller
Selfhosted @lemmy.world Have you tried self-hosting your own email recently?
Programming @programming.dev Where's the Shovelware? Why AI Coding Claims Don't Add Up
Rust @programming.dev things rust shipped without (2015)
Technology @beehaw.org Forum User Returns After 100,000 Hour Ban to Continue the Same Argument That Got Them Banned in 2013
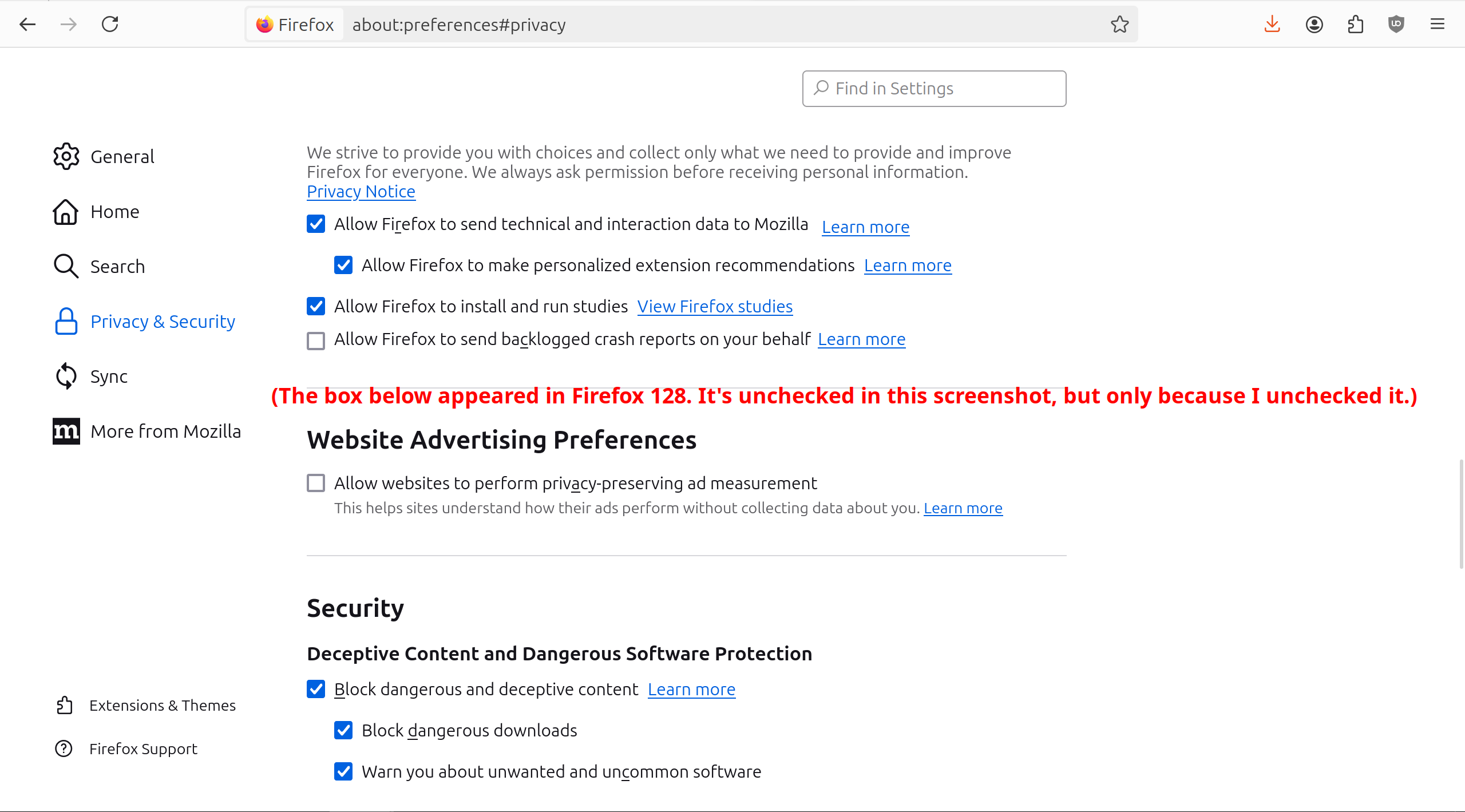
Privacy @lemmy.ml Firefox added ad tracking and has already turned it on without asking you
Software Gore @lemmy.world This message does not exist
Technology @beehaw.org Quad9 Turns the Sony Case Around in Dresden
Steam Hardware @sopuli.xyz Good Times
Selfhosted @lemmy.world How can I spy on myself?
ADHD @lemmy.world FDA approves multiple generics of Vyvanse
Electronics @discuss.tchncs.de Privacy friendly ESP32 smart doorbell with Home Assistant local integration









Yes: https://en.wikipedia.org/wiki/High-bandwidth_Digital_Content_Protection